Basic Debian 11 server installation hardening
Today we will customize ssh, network and file permissions on fresh Debian 11 install.
- SSHD customization
- Network customization on sysctl.conf
- Linux Firewall – todo
- Manage password policies – todo
- User / Group permissions
1. Securing SSHD access
- Change default 22 port to something else. I have changed to port 2222
SSH port 22 to 2222 port
sudo su
nano /etc/ssh/sshd_config
Port 2222- Disable remote ssh access for root user
Disable remote root login
PermitRootLogin no- Select users who can login via ssh
AllowUsers [username]
AllowUsers fullstackadmin fullstackuser1And some final sshd_config customization
- Protocol 2
- IgnoreRhosts
- HostbasedAuthentication
- PermitEmptyPasswords
- X11Forwarding
- Ciphers
- ClientAliveInterval
- ClientAliveCountMax
- UsePAM
So still in config of sshd in ‘/etc/ssh/sshd_config’
Protocol 2
IgnoreRhosts yes
HostbasedAuthentication no
PermitEmptyPasswords no
X11Forwarding no
MaxAuthTries 4
Ciphers aes128-ctr,aes192-ctr,aes256-ctr
ClientAliveInterval 900
ClientAliveCountMax 0
UsePAM yes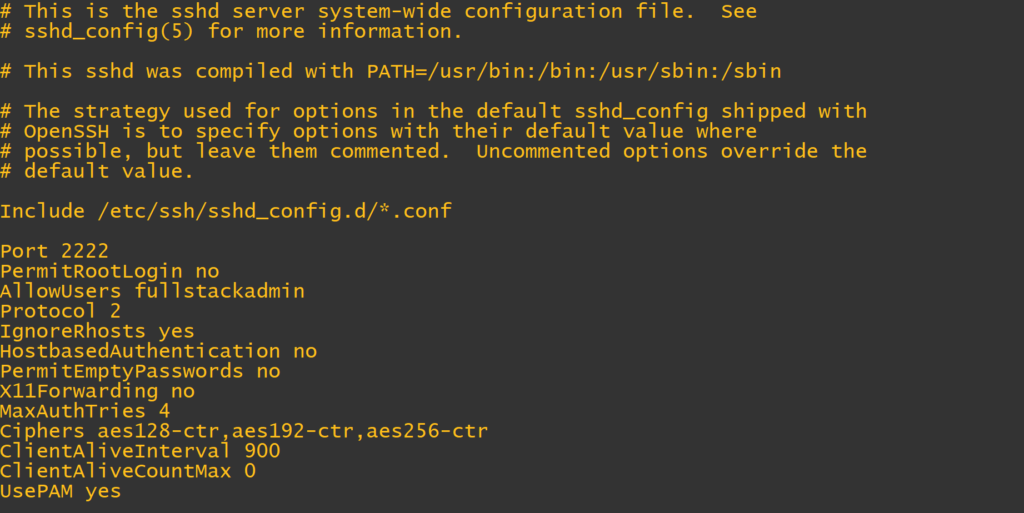
Save config and restart sshd daemon.
systemctl restart sshChange owner and file permissions of sshd config
chown root:root /etc/ssh/sshd_config
chmod 600 /etc/ssh/sshd_config2. Customize network settings in sysct.conf
- Disable ip forwarding net.ipv4.conf.all.send_redirects and net.ipv4.conf.default.send_redirects to 0 in ‘/etc/sysctl.conf’
- Disable Send Packet Redirects net.ipv4.conf.all.accept_redirects and net.ipv4.conf.default.accept_redirects to 0 in ‘/etc/sysctl.conf’
- Enable Bad Error Message Protection setting net.ipv4.icmp_ignore_bogus_error_responses to 1 in ‘/etc/sysctl.conf’
Edit ‘/etc/sysctl.conf’
nano /etc/sysctl.conf
net.ipv4.conf.all.send_redirects = 0
net.ipv4.conf.default.send_redirects = 0
net.ipv4.conf.all.accept_redirects = 0
net.ipv4.conf.default.accept_redirects = 0
net.ipv4.icmp_ignore_bogus_error_responses = 1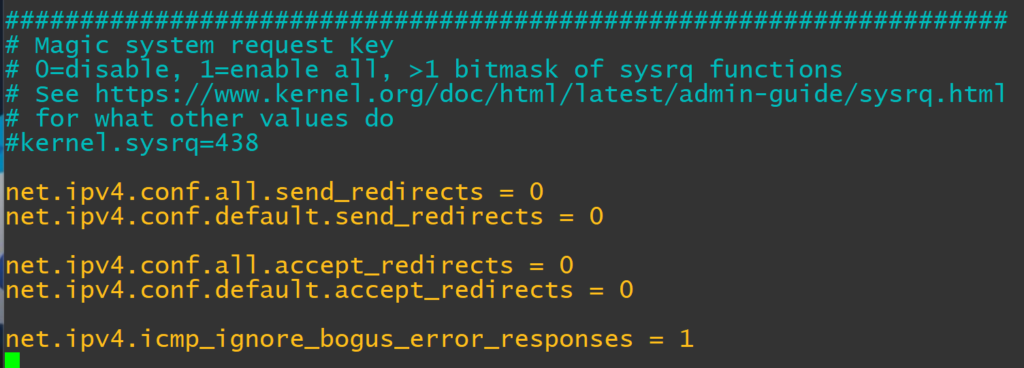
3. Change file permissions and owner of cron, passwd, group, shadow and gshadow files
User/Group Owner and Permissions on ‘/etc/anacrontab’, ‘/etc/crontab’, ‘/etc/cron’
chown root:root /etc/crontab
chmod og-rwx /etc/crontab
chown root:root /etc/cron.hourly
chmod og-rwx /etc/cron.hourly
chmod og-rwx /etc/cron.daily
chown root:root /etc/cron.daily
chown root:root /etc/cron.weekly
chmod og-rwx /etc/cron.weekly
chown root:root /etc/cron.monthly
chmod og-rwx /etc/cron.monthlyPermissions on ‘passwd’ file
chmod 644 /etc/passwd
chown root:root /etc/passwdPermissions on ‘group’ file
chmod 644 /etc/group
chown root:root /etc/group Permissions on ‘shadow’ file
chmod 600 /etc/shadow
chown root:root /etc/shadowPermissions on ‘gshadow’ file
chmod 600 /etc/gshadow
chown root:root /etc/gshadowOriginal post : https://www.pluralsight.com/blog/it-ops/linux-hardening-secure-server-checklist
Thanks. I hope it will help you to progress your skills.